Confidential Tables Setup
With the Confidential Data Protection extension you can protect your confidential data from being exposed to Business Central users in your company that should not have access to this data.
Confidential Tables Setup Page¶
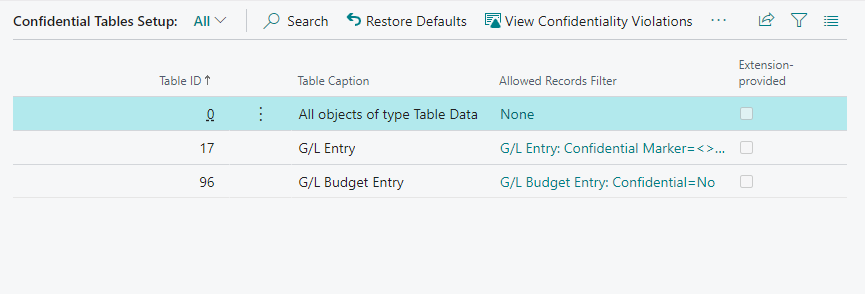
The extension allows you to specify the tables that have data that should not be directly accessible to all Business Central users. On the Confidential Tables Setup page you can find which tables are considered as containing confidential data.
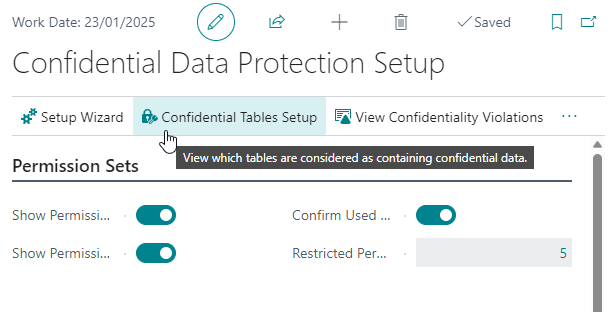
As an administrator you can view the setup by opening this page using the Confidential Tables Setup action on the Confidential Data Protection Setup page.
By default, the G/L Entry table and G/L Budget Entry tables are considered to contain confidential tables (N.B. when no extensions or customizations have been applied). This means that Table Data Direct Read permission assignments for these tables are considered confidentiality-violating permission assignments as they would grant users access to confidential data in Business Central.
For tables where only some records contain confidential data, the Allowed Records Filter field is used to specify which records are allowed to be accessed by users, i.e., which records in the table are non-confidential.
Important
Note that permission assignments that grant access to all table data (i.e., a permission assignment for table ID = 0) are always considered to expose confidential table data.
The Restore Defaults action on the Confidential Tables Setup page can be used to easily apply the default confidential tables setup (e.g., when extensions to the defaults have been added or removed).
The View Confidentiality Violations action can be used to identify and resolve confidentiality-violating permission set assignments to users based on the Confidential Tables Setup configuration. For more information on how you can use this action, please see the Identify and Resolve Violations section in the user manual.
Confidential Permission Sets¶
Based on the Confidential Table Setup configuration, the Confidential Data Protection extension can identify which permission set pose a risk to exposing confidential data to your Business Central users.
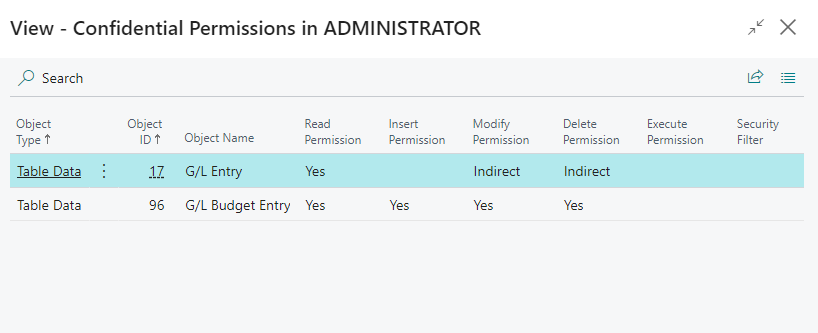
A permission set is considered as exposing confidential data when one of the effective permissions of the permission set grant TableData Direct Read permissions for a table that has been configured on the Confidential Table Setup page.
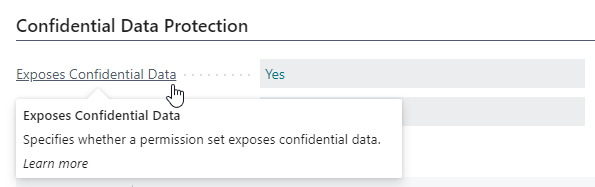
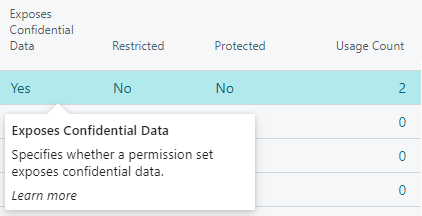
The Confidential Data Protection tab on the Permission Set card page contains an Exposes Confidential Data field which specifies whether the permission set exposes confidential data through one of its effective permissions.
By drilling down on the field value (i.e., by clicking on Yes), you can see which effective permissions the Confidential Data Protection extension identified as exposing confidential data.
Tip
If you have enabled the Show Permission Set Properties setting on the Confidential Data Protection Setup page, then a Exposes confidential Data field will be available on the Permission Sets page which specifies for each permission set whether it exposes confidential data through one of its effective permissions. Note that you can also sort and filter the list page on this field.
Confidential Data Exclusion Permission Set¶
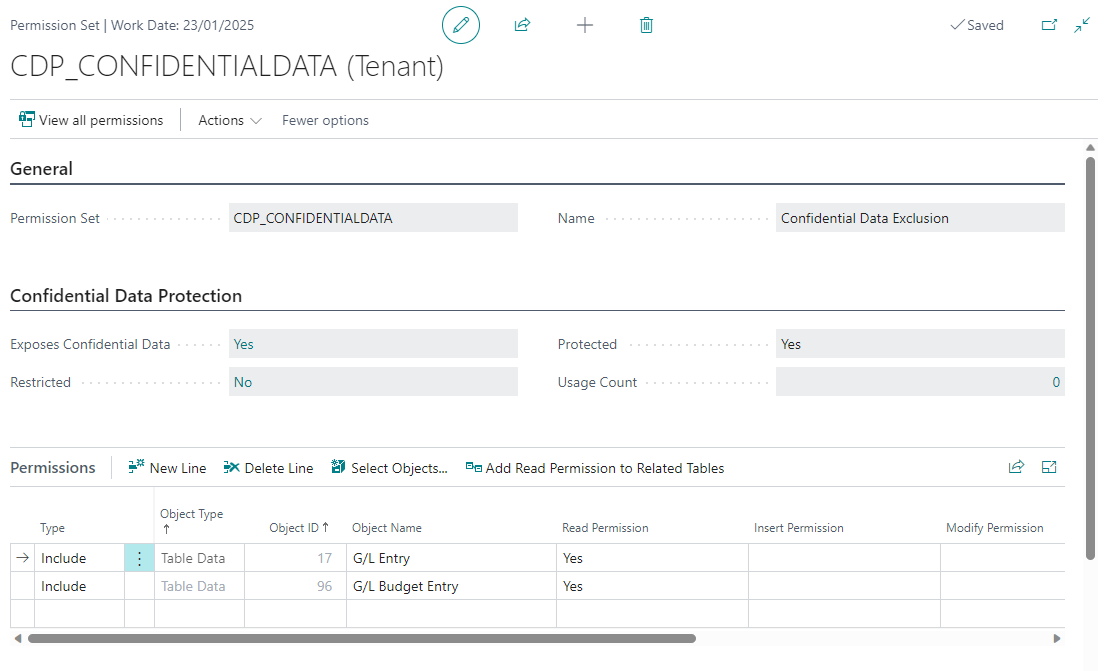
From the Confidential Tables Setup configuration, a Confidential Data Exclusion permission set is generated and updated automatically whenever the configuration is changed by an administrator. You can view this permission set by invoking the Confidential Data Exclusion Permission Set action on the Confidential Tables Setup page.
The Confidential Data Exclusion permission set is used to exclude Table Data Direct Read permission assignments from permission sets that expose confidential data (according to how this is defined on the Confidential Table Setup page).
Restricted Permission Sets¶
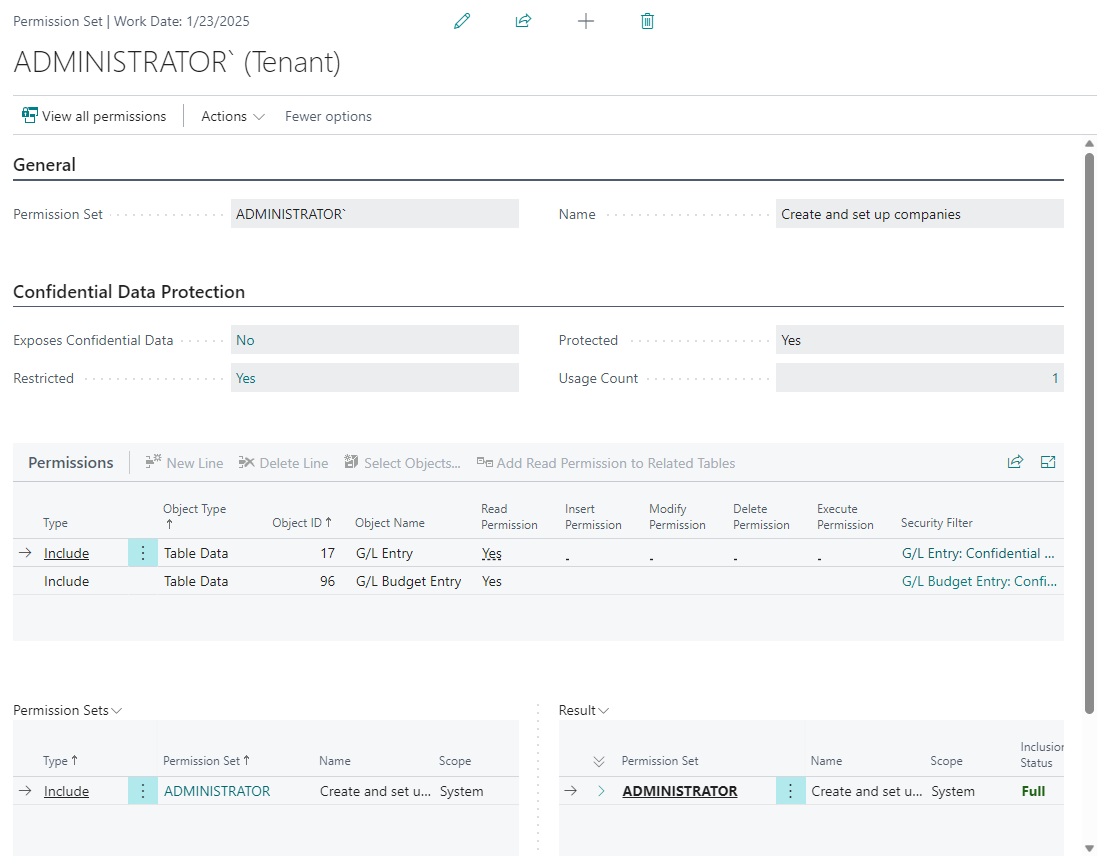
If a permission set is assigned to a user or group of users (i.e., a security group) which would expose confidential data to users, then a Restricted permission set will be generated automatically and the permission set assignment will be replaced automatically with an assignment of the newly generated, restricted permission set.
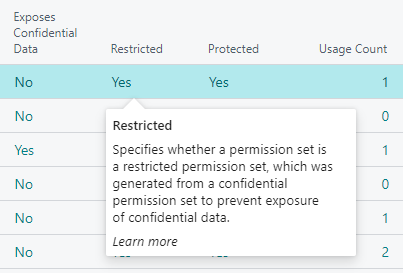
A Restricted permission set is a permission set in which the access that would be granted to confidential tables has been restricted, making them safe to assign to users without exposing confidential data. If an attempt is made to assign a permission set that would expose confidential data to users, then a restricted permission set will be generated which includes the original permission set and excludes the Confidential Data Exclusion permission set. The restricted permission set is then assigned to the user instead of the confidential permission set.
Tip
-
You can open an overview of all Restricted permission sets by invoking the Restricted Permission Sets action on the Confidential Data Protection Setup page.
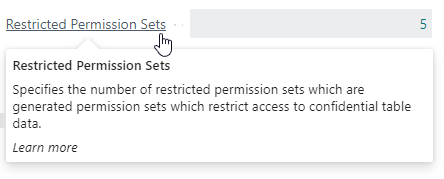
Or, using the drilldown of the Restricted Permission Sets field on the Confidential Data Protection Setup page.
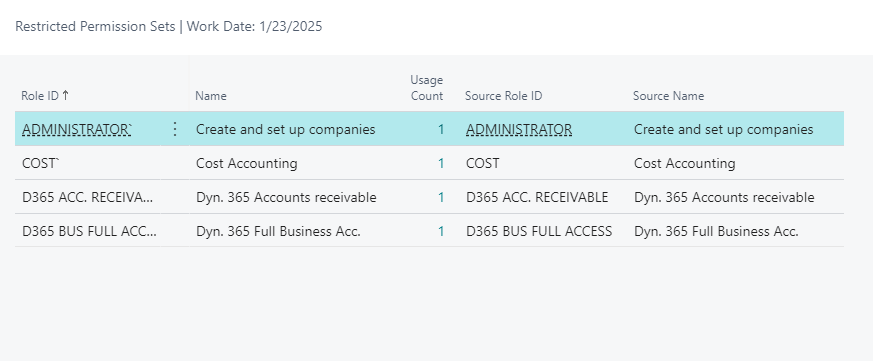
This will open a page where you can view all restricted permission sets in your Business Central environment.
On this page you can also view the Confidential (source) permission set that the Restricted permission set was derived from, if any, and how many times the permission set is used/assigned.
-
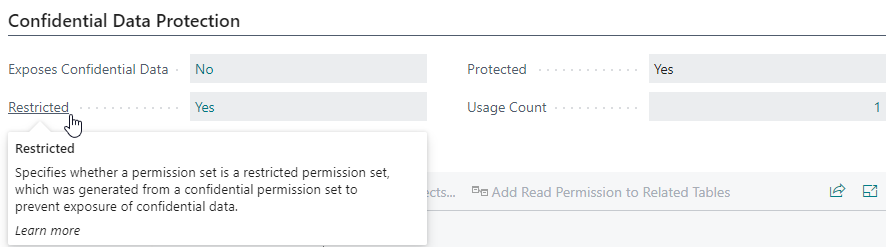
The Confidential Data Protection tab on the Permission Set card page also shows whether a permission set is a restricted permission set.
-
If you have enabled the Show Permission Set Properties setting on the Confidential Data Protection Setup page, then a Restricted field will be available on the Permission Sets page which specifies for each permission set whether it is a restricted permission set.
Note that you can also sort and filter the list page on this field.
Demo Video¶
Watch the "Set up Confidential Tables" section of our demo video to learn more about the Confidential Tables Setup.